New SEC Cybersecurity Disclosure Rules: What Businesses Should Do

Cybersecurity operations and reporting are entering a new phase of rigor because of controversial cybersecurity disclosure rules from the Securities and Exchange Commission (SEC). Taking effect now, the rules requires publicly traded businesses to publicly disclose cybersecurity incidents within four business days of determining that the incident is material; and report on their cybersecurity risk management and governance processes. In effect, the SEC has put businesses on notice that they will be held accountable for failing to manage and report cybersecurity – even while imposing myriad and opaque requirements in a 200-world ruling.
These rules represent a significant step towards greater accountability and transparency in handling cybersecurity threats and incidents. Companies are advised to review and update their disclosure policies, conduct cybersecurity risk assessments, develop comprehensive incident response plans, invest in cybersecurity tools and training, and establish clear communication channels to ensure compliance with these new regulations.
And yes, that sounds like a big requirement, but businesses should be safeguarding themselves anyway, whether the SEC mandates them to do so or not. The average cost of a single data breach is $4.45 million – with industries such as healthcare incurring an average cost as high as $10.93 million per breach.
At Centific, we believe that an intelligent application of generative AI with human oversight can be enormously valuable to help businesses comply and to improve their digital safety.
Let’s take a closer look at what’s happening and what businesses should do.
What the SEC Requires – and Penalties for Non-Compliance
The SEC’s new cybersecurity disclosure rules, proposed in July 2023, bring significant changes to how publicly traded companies manage and report cybersecurity incidents. The rules are complex, but here are a few of the key points every business needs to know about:
Faster and More Detailed Incident Reporting
Publicly traded companies are now required to report “material cybersecurity incidents” within four business days of determining the incident’s materiality. This is a major shift from the previous vague requirement of “prompt” reporting, which often led to delays and inconsistencies. The initial reports must include detailed descriptions of the incident, such as the nature of the attack, affected systems, the potential impact on operations and finances, and the remedial measures taken.
Annual Disclosure of Cybersecurity Processes and Governance
In addition to incident reporting, companies must now disclose (in their annual reports) their cybersecurity risk management policies, governance procedures, and incident response plans. This includes detailing processes for assessing, identifying, and managing material risks from cybersecurity threats, the role of the board and management in cybersecurity governance, and how these processes are integrated into overall risk management systems.
Impact on Company Roles
The new rules have amplified the roles of company executives like CFOs, general counsels, CEOs, and board members in terms of ensuring cybersecurity risk management and compliance with the disclosure requirements.
Enhanced Transparency and Investor Protection
These rules aim to provide investors with consistent, current, and useful information about how companies manage cyber risks, thereby enhancing transparency and accountability in the corporate sector. As we have seen time and again, cybersecurity breaches can cause significant damage to a company’s financial health – a recent example being the notorious hack of MGM Resorts International, which incurred a $100 million hit on the company’s quarterly results.
The SEC has not yet issued any specific penalties for failing to adhere to the new cybersecurity disclosure rules. However, the SEC has broad enforcement authority and can use a variety of tools to penalize companies that violate its rules, including the imposition of civil fines of up to $25 million. The SEC can invoke many other disruptive penalties such as ordering companies to cease and desist from violating its rules and suspend a company’s trading privileges if it believes that the company is not complying with its disclosure obligations.
But, there’s something else to consider: the new rule will also make it more likely that businesses will be sued by investors or other stakeholders if they fail to disclose a material cybersecurity incident. When the SEC puts a stake in the ground and a business does not comply, activist investors in particular are given a proof point for taking a position against a company.
It is important to note that the new cybersecurity disclosure rules are just one part of the SEC’s broader effort to address cybersecurity risks in the securities markets. The SEC has also taken a number of other steps to address cybersecurity risks, such as issuing guidance on how companies should conduct cybersecurity risk assessments and requiring companies to have written cybersecurity policies. And the SEC recently made a very strong statement about cybersecurity compliance by charging SolarWinds and its chief information security officer (CISO) with fraud and internal controls failures. The SEC says that SolarWinds and its CISO defrauded investors by overstating SolarWinds’ cybersecurity practices and understating or failing to disclose known risks.
Controversies about the SEC Cybersecurity Disclosure Rules
The new SEC cybersecurity disclosure rules have faced several criticisms:
Materiality Determinations and Reporting Timelines
One of the criticisms is related to the requirement for companies to make materiality determinations “without unreasonable delay” after discovering a cybersecurity incident. Critics argue that the requirement to report material cyber incidents within four business days after determining their materiality is challenging. After all, it takes on average 277 days to identify and contain most data breaches. The breadth, impact, and origin of an incident can be difficult to determine in a few days, and rushing this process could lead to inaccurate reporting.
Challenges in Disclosure
Companies are faced with the challenge of deciding what to disclose. There’s a balance to strike between providing enough detail for compliance and not revealing too much that might jeopardize security.
Concerns about Public Safety and National Security
There have been concerns that early public disclosures of cyber incidents could undermine criminal and other investigations. The rule provides a solution where the Attorney General can delay disclosure if it poses a substantial risk to national security or public safety, but this has been seen as impractical and limited in scope.
But regardless of the controversies, the rules are now in place. Companies need to do their best to comply.
What Businesses Should Do about the SEC Cybersecurity Disclosure Rules
Businesses should look at the disclosure rules as an opportunity to review their cybersecurity practices and improve them. By the time a business is required to report them in their annual report per the SEC rules, they should have been adhering to rigorous cybersecurity practices, anyway. We recommend that businesses:
- Understand your security posture, or your overall state of cybersecurity readiness. A security posture includes, among other things, technological controls (e.g., firewalls, intrusion detection and prevention systems, encryption technologies, and other security hardware and software solutions) and access controls (ensuring that only authorized individuals and devices can access certain information). The security posture may be assessed via Purple Teaming, adopting gen AI for a tabletop exercise. The tabletop exercise can reveal improvement opportunities in incident management, technological controls, and access controls
- Consider adopting or strengthening a zero trust architecture, which assumes that threats can exist both outside and inside the traditional network perimeter, thus necessitating rigorous verification and control measures. As a result, a company employing SecOps powered with gen AI accelerates the improvement of ZTA, thus protecting its systems with a far greater level of rigor. The SEC is adopting a ZTA at the behest of the Office of Management and Budget by a deadline of September 30, 2024. This is the gold standard.
- Create a stronger bridge between the cybersecurity and digital fraud teams, which typically operate separately. A combined approach can improve overall security posture, enhance user trust, and streamline compliance efforts. Centific’s point of view of infusing a digital safety team facilitates and strengthens the efforts between cybersecurity and digital fraud teams. The digital safety team may consist of Purple Teams, SecOps, and FraudOps, all of which mitigate fraud early during reconnaissance
- Test the effectiveness of your recovery plans including how quickly you report breaches. This is typically done through a tabletop exercise, or a simulated incident response activity where participants discuss and work through a hypothetical cyberattack scenario. It’s like a war game for cybersecurity, but instead of using physical models and maps, it’s all done verbally around a table. This will help you answer questions such as whether you have a clear plan for how to handle a cyberattack and whether everyone is on the same page about their roles and responsibilities.
How Generative AI Can Help
We believe that generative AI can play a crucial role in helping businesses manage all the requirements of cybersecurity governance and disclosure. Let’s look at tabletop exercises, for example. Gen AI can create realistic scenarios and test cybersecurity defenses more effectively than humans can. If a company wants to test its vulnerability to ransomware infection and its responsiveness to an attack, gen AI, if trained properly, can simulate a ransomware attack that encrypts critical data and disrupts operations, presenting challenges in decision-making under pressure, such as whether to pay the ransom. In the realm of cloud breach security, gen AI could model a breach in cloud services used by the organization, leading to data leakage and service disruption, with the objective of testing how well the team deals with cloud-specific security challenges.
Gen AI can help businesses plan for what exactly needs to be reported to the SEC. For instance, a good gen AI tool can scan complex SEC documents stipulating reporting requirements and create, faster and more accurately than a person – a templatized format for reporting. For example, consider the guidelines provided below by the SEC:
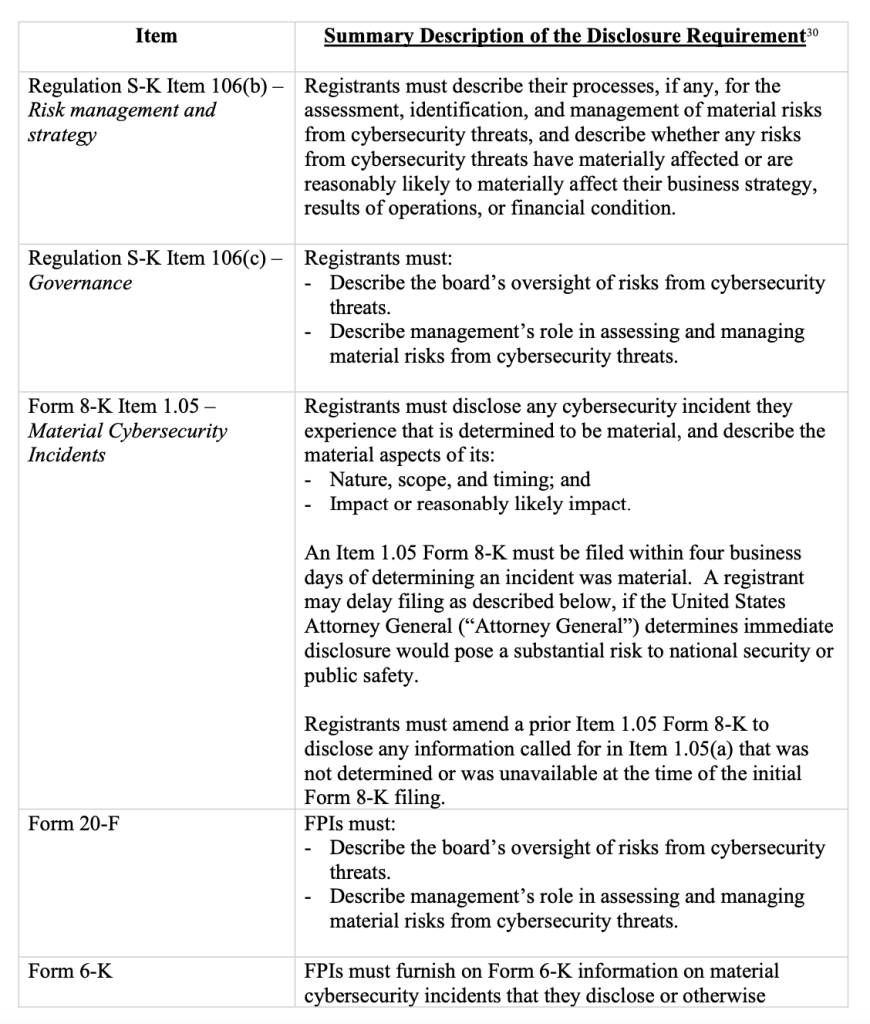
Now, it’s easy to see how gen AI could make it possible for a business to create a repeatable template for reporting these things and then help a team research, verify, and document the actual content requested.
But this brings me to another important component: human oversight for training gen AI to do its job and to ensure accuracy and completeness in all the ways gen AI is used, including tabletop scenario planning in general and SEC reporting specifically. Gen AI can also help a company test whether its reporting is disclosing too much based on pre-defined rules on what is not permissible.
We’re living at an important and precarious time for cybersecurity. The stakes are high. The right combination of gen AI and human oversight can help businesses comply with the SEC – and protect themselves.
