How Google Magika Can Help Healthcare Systems Fight Malware

The healthcare industry has a malware problem. And Google may have a solution: Magika, an AI-powered file-type identification system. Magika, unveiled recently on Google’s blog, can bolster a business’s defense against malware in several ways. The tool’s ability to accurately identify file types may prove to be a breakthrough for businesses to detect threats and prevent potential attacks. For the healthcare industry, Magika could be especially crucial. The average cost of a cybersecurity breach in healthcare is the highest of any industry, and cybersecurity breaches are literally a life-or-death problem in healthcare. Magika just might help save a life.
The Cybersecurity Threat to Healthcare
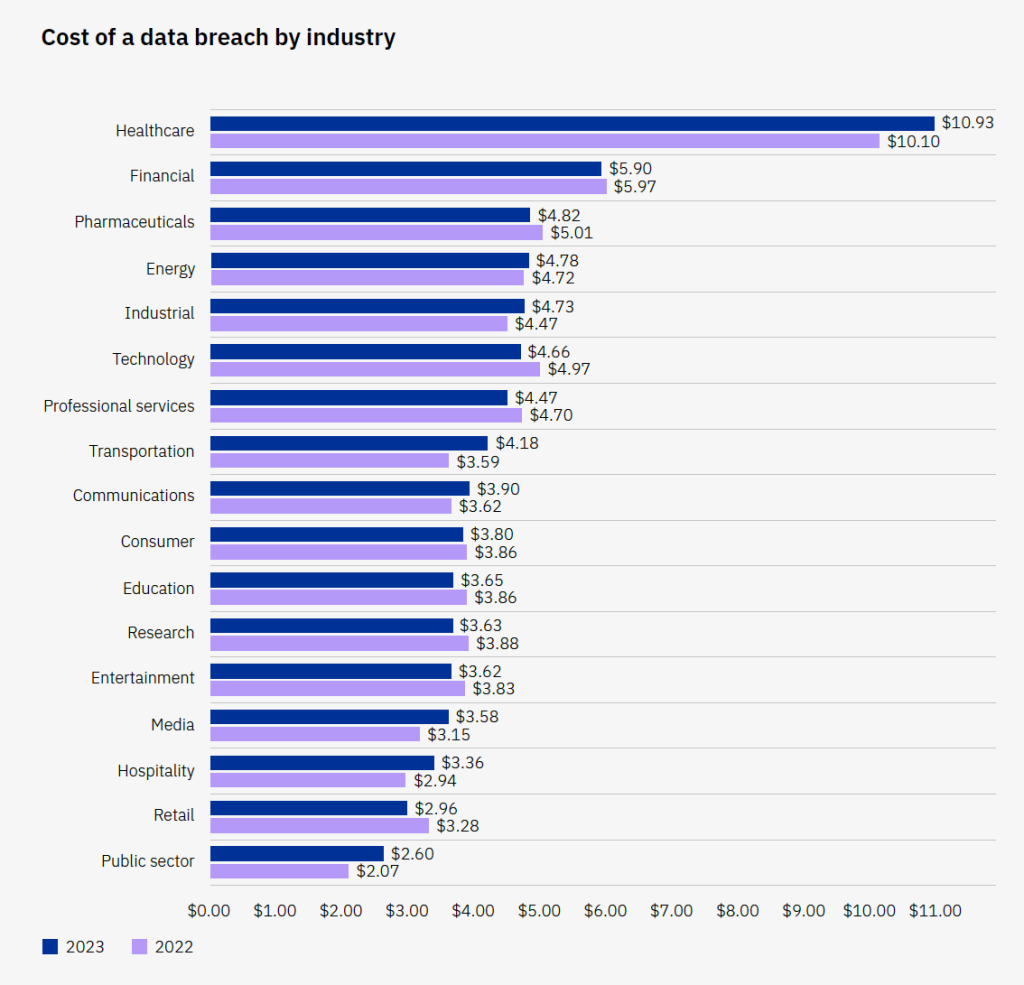
One cannot overstate the magnitude of the cybersecurity problem in healthcare. According to the IBM Average Cost of a Cybersecurity Breach, for the 13th year in a row, the healthcare industry reported the most expensive data breaches, at an average cost of $10.93 million. Since 2020, healthcare data breach costs have increased 53.3 percent.
The cost to healthcare goes beyond financial. Human lives are at stake. Let’s look at ransomware attacks as an example. According to Hannah Neprash of the University of Minnesota School of Public Health, during a ransomware attack, in-hospital mortality goes up about 20 percent to 35 percent when a hospital goes through a ransomware attack. That’s because ransomware attacks cripple a hospital’s operations, and this means halting medical care. For example, a ransomware attack on two hospitals in late 2023 forced them to divert patients coming in for emergency care to other facilities and to postpone elective surgeries. A ransomware attack had victimized one of the hospitals, Hackensack Meridian, in 2019. Unfortunately, paying the ransom did not prevent future attacks, as the 2023 example illustrates.
Healthcare Under Attack
All told, ransomware attacks affected at least 141 hospitals in 2023. By 2023, the typical ransom amount soared by 29,900 percent, reaching approximately $1.5 million. This surge in ransomware profits has enabled cybercriminal gangs to expand their operations, finance the acquisition of initial access points, and invest in zero-day exploits, leading to an uptick in the frequency of attacks. In an effort to intensify their pressure, some groups have resorted to more extreme measures, including directly contacting individuals and demanding payments. For instance, there have been incidents where attackers targeted cosmetic surgery clinics, leaked sensitive photos online, and then extorted the patients by demanding payments to remove these images from the web. In one specific case, a ransomware group threatened to publish personal data of patients unless they received $50 for each patient to prevent the data release.
Ransomware attacks are only part of the problem. Several cybersecurity breaches are threatening the healthcare industry, including:
- Phishing attacks (a very popular method for gaining access to healthcare systems).
- Insider threats (either the deliberate or accidental leaking of data from an employee).
- Third-party vendor breaches (healthcare organizations rely on many third-party vendors for software, support, and data storage).
- Network infiltration and hacking (attackers actively find and exploit vulnerabilities in a healthcare organization’s networks or websites).
- Unpatched vulnerabilities (outdated software, operating systems, and medical devices often have known vulnerabilities that cyber criminals can target).
Oftentimes, bad actors will use a combination of these techniques to increase their chances of success.
Why Healthcare Is Vulnerable
The healthcare industry is especially vulnerable, too. For one thing, healthcare organizations process data that bad actors covet. Medical records contain a treasure trove of personally identifiable information (names, addresses, Social Security Numbers), detailed medical histories, and insurance data. Hackers sell this on the dark web or use it for identity theft, extortion, or targeted scams. Healthcare facilities (especially academic hospitals) may also possess valuable research data and intellectual property crucial for developing new medications and treatments. This often attracts interest from bad actors, including nation-state bad actors.
Healthcare organizations are vulnerable for other reasons, too. The complex digital tapestry of hospitals – with vast networks, numerous connected Internet of Things (IoT) medical devices, and electronic health records (EHRs) – increases the attack surface that hackers can exploit. Unfortunately, older healthcare systems struggle to integrate with new technologies and cannot receive adequate security updates. This creates openings for an attack and expands the blast radius, or potential damage caused by a cybersecurity breach. Budget constraints or the reliance on critical equipment tied to legacy systems hinder rapid change. Phishing scams, clicking suspicious links, or accidental mishandling of data creates exploitable security gaps. Healthcare workers may not be well-versed in cybersecurity best practices, leaving the network vulnerable.
So, why does Magika from Google matter in context of this complicated scenario?
A Breakthrough in Fighting Malware
To understand why Magika matters as a tool to fight cybersecurity breaches, we must first understand the role that malware plays in these breaches.
Malware is a central tool that bad actors use to execute many of the most common cybersecurity breaches in healthcare described above. For example, with phishing attacks, bad actors often malware as a payload in phishing emails or disguised as legitimate downloads in files such as PDFs, ZIP files, Microsoft Office documents, and more. Ransomware itself is a complex and malicious type of malware designed to encrypt data. And with network infiltration and hacking, bad actors frequently use malware to exploit vulnerabilities, gain initial access to networks, and then steal data or install backdoors for further compromise. When we talk about phishing, ransomware, or network exploits, malware is often a major component in how those attacks succeed.
How Healthcare Systems Fight Malware
Healthcare systems deploy a suite of specialized tools to combat the persistent malware threat. For example, endpoint protection platforms (EPP) form the frontline defense on systems like desktops, laptops, and servers. EPPs combine traditional antivirus capabilities with more advanced techniques like behavioral analysis (identifying potentially malicious actions), heuristic detection (searching for patterns suggestive of malware), sandboxing (running suspicious files in isolated environments to observe activity), and machine learning models for evolving threat detection.
On the other hand, data loss prevention (DLP) tools are designed to control and monitor sensitive data flow within and outside of the healthcare system. DLP Identifies and potentially blocks actions that could result in data leakage, helping prevent accidental or malicious data exfiltration.
Healthcare systems may rely on other approaches, too, such as:
- Intrusion Detection and Prevention Systems (IDS/IPS): these monitor network traffic for anomalies and malicious signatures. An IPS can actively block or quarantine threats, while an IDS provides alerts for further investigation.
- Firewalls: hardware or software firewalls filter network traffic to prevent unauthorized access, acting as a gatekeeper for network perimeter security.
- Email security gateways: protect against phishing attacks and malware delivered via email. They scan attachments and links, block known malicious senders, and quarantine suspicious emails.
Magika from Google does not replace any of those approaches; rather, Magika complements them by identifying the type of file(s) a healthcare organization is storing or processing. Cybersecurity teams can then use this information to inform other security decisions, such as how to handle the file or whether it should be scanned for malware.
The Magic Behind Magika
As I noted above, malware disguises itself by hiding in a variety of file types. As Google points out on its blog, accurately detecting file types has been crucial in determining how to process files. By identifying a file type, a business can fight cybersecurity threats more effectively.
For instance, businesses can implement more effective security filters and monitoring systems. Identifying file types enables the application of specific security policies to different types of files, such as blocking or scanning executable files (.exe) or scripts (.js, .vbs) that bad actors commonly use for malware delivery.
Accurate file type identification also allows for more targeted antivirus scanning. Antivirus software can be configured to perform deep scans on file types that are more likely to contain malware, thereby improving detection rates and reducing the time required for scanning.
Understanding the types of files entering and exiting an organization’s network helps in assessing the risk levels associated with them. Certain file types are inherently riskier than others due to their ability to execute code or scripts. Identifying these file types helps in prioritizing security efforts.
And in the event of a security breach, accurately identifying the types of files involved can aid in the forensic analysis and help in understanding the attack vectors used. This information is crucial for mitigating the current attack and preventing future incidents.
Why It Is Difficult to Identify File Types
But accurately identifying file types is difficult. That’s because each file format has a different structure, or no structure at all. This is particularly challenging for textual formats and programming languages as they have very similar constructs. Unfortunately, largely manual approaches for detecting file formats are error prone and time consuming. Meanwhile, bad actors are constantly attempting to confuse detection with adversarially-crafted payloads.
But Magika does what human beings acting alone cannot. As Google puts it:
To address this issue and provide fast and accurate file-type detection we researched and developed Magika, a new AI powered file type detector. Under the hood, Magika uses a custom, highly optimized deep-learning model designed and trained using Keras that only weighs about 1MB. At inference time Magika uses Onnx as an inference engine to ensure files are identified in a matter of milliseconds, almost as fast as a non-AI tool even on CPU.
How a Hospital Could use Magika
A hospital could conceivably use Magika to protect itself in many ways. For instance:
Email Security
Magika could automatically scan incoming emails and their attachments for malicious file types, ensuring that only medical staff opens only safe documents. For example, let’s say a phishing email arrives in the inbox of a hospital employee. The email appears legitimate, perhaps mimicking a message from a known medical supplier or partner organization. It contains an urgent-looking attachment, such as an “updated invoice” or “critical delivery schedule.”
Standard security software might scan the attachment. But if a bad actor has carefully designed ransomware to evade signature-based detection, it may not be recognized. But Magika could be integrated into the hospital’s email system to automatically scan and analyze incoming emails and their attachments for known and unknown file types. Magika would use AI to accurately identify file types that could potentially harbor malware, such as executable files disguised as harmless documents. If a suspicious file were detected, Magika could automatically block the attachment from being opened and alert the IT security team for further investigation, thus preventing the spread of malware and protecting sensitive data.
Patient Data Protection
Magika could identify and block potentially harmful files from being uploaded to patient records systems, thus safeguarding sensitive health information from malware that a bad actor could use to compromise data integrity or privacy. Let’s say a medical staff member attempts to upload a document to a patient’s electronic health record (EHR) system. Unbeknownst to them, the document (perhaps something received from an external source or unknowingly downloaded) contains hidden ransomware code. Basic file type checks or simple antivirus scans might fail to detect the ransomware if it’s well-disguised within the document. Magika would distinguish between legitimate document types and those masquerading as such but potentially containing malware. If a file were deemed hazardous, Magika would block its upload and alert the cybersecurity team.
Incident Response
Magika could quickly identify the file types involved in a security breach, aiding in the swift containment and analysis of the attack vector. Following a security breach, Magika would scan and identify the types of files involved, allowing for a swift determination of the malware’s nature and its entry method. This would enable the IT security team to quickly contain the breach, remove the malicious files, and prevent further spread by closing the exploited vulnerabilities.
Hospitals could also use Magika for scenarios like ensuring secure file sharing between departments, preventing malware in downloadable patient forms from external websites, and safeguarding medical research data by accurately identifying and blocking the upload of malicious files. Additionally, a healthcare system can use Magika to recognize and handle secure file types, enhancing overall cybersecurity awareness and practices within healthcare settings.
Google says that Magika plays a pivotal role in enhancing user safety by directing emails, documents, and files from Gmail, Drive, and safe browsing to appropriate security and content policy checks. Analyzing an average weekly volume of several hundred billion files, Magika boosts the precision of file type recognition by 50 percent over the previous system, which was based on manually created rules. Specifically, this improvement in precision enables an 11 percent increase in the number of files examined by advanced AI scanners for malicious documents, while simultaneously reducing the fraction of unclassified files to 3 percent.
Next Steps
Magika is not a silver bullet to fight malware, but the introduction of Magika should be a wake-up call for hospitals to step up their efforts. We suggest that healthcare organizations take a number of steps that include:
- Strengthen your security posture with a zero trust architecture (ZTA): ZTA seeks to protect an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. We discuss ZTA in our blog post “Should Your Business Adopt a Zero Trust Architecture?”
- Implement advanced detection tools: integrate AI-based tools like Google Magika for enhanced file type identification and threat detection.
- Test your security posture with Purple Teaming: Purple Teaming identifies cybersecurity gaps and control measures through attack simulations. With Purple Teaming, one team from your cybersecurity organization simulates both attacks on cybersecurity perimeters and their defense. Each team member plays both the role of attacker and defender, which ensures a more robust and intricate breach/attack simulations.
- Train staff: conduct ongoing cybersecurity training for all staff to recognize potential threats.
- Update and patch systems: regularly update IT systems and software to mitigate vulnerabilities.
- Access control and user permissions: limit file access based on roles to reduce the risk of internal threats.
- Have an incident response plan: Develop and regularly update an incident response plan to swiftly address breaches.
Centific can help hospitals in the fight against malware. Click here to learn more about our digital safety capabilities.
